❧ More and More Businesses Now Operate Online
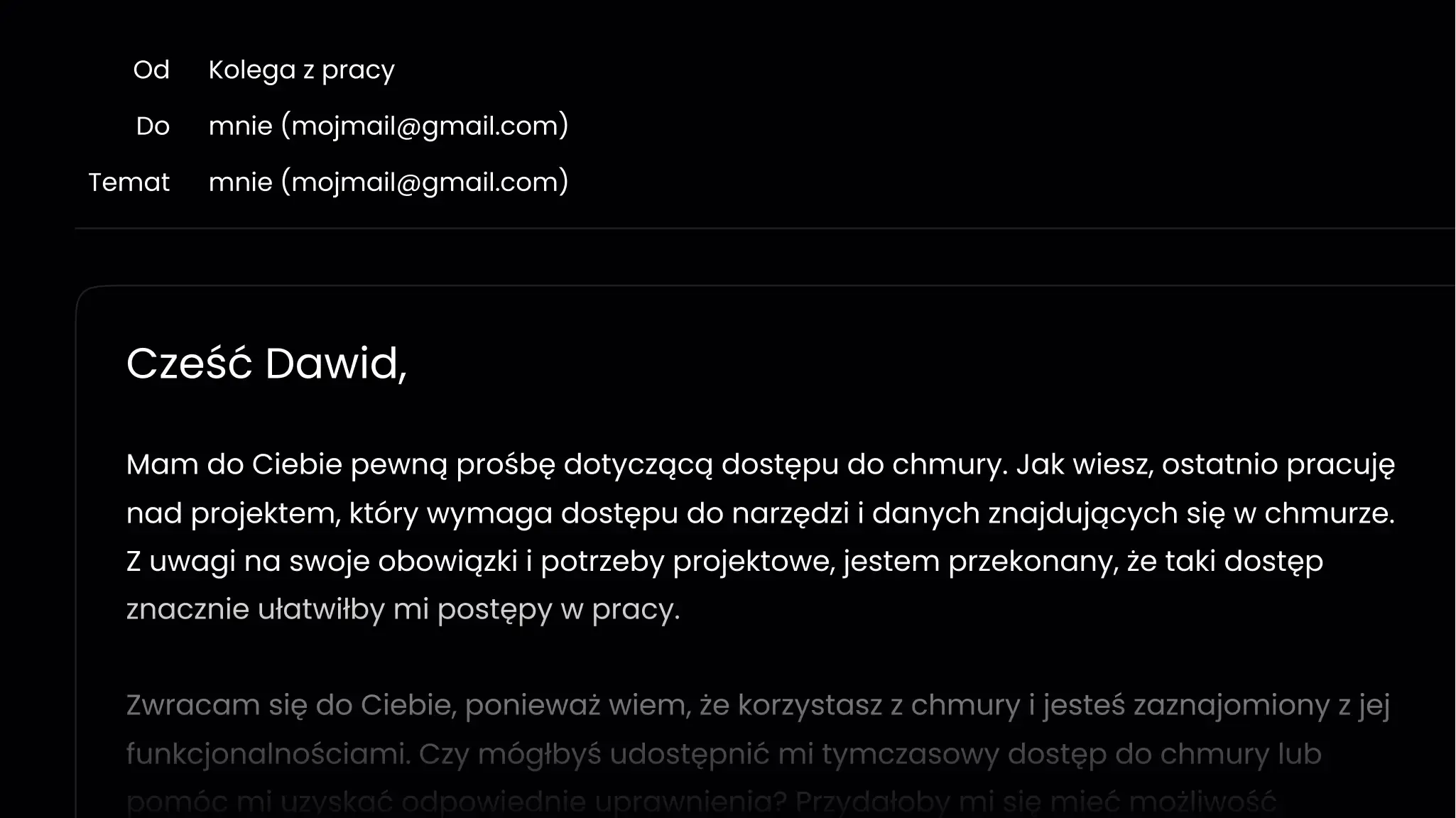
Across studies in enterprises big and small, one pattern keeps appearing: to get into a company system, attackers sometimes just… politely and convincingly ask a “teammate” for the password.
In most attacks, hackers target everyday employees who—unaware of the risk—grant unauthorized access to confidential data. For criminals, that’s a perfect profit machine.
How do you avoid becoming a victim? Read on to learn how to feel safer online.
❧ The Cybercriminal—Is There Really Something to Fear?
The “hacker”: that shadowy figure you hear about whenever another sensitive database leaks. Who are they, really—just a boogeyman, or a real threat?
Plenty of people have learned the hard way that a single moment of inattention online can be very expensive. One careless click ☝️ or swipe in the wrong place and… whoosh! Someone gets your login credentials, or someone captures your credit card number and locks you out.
Cybercriminals act alone or in organized groups. Their attacks are deliberate, not random. They’re professionals who know exactly how to get a user to do what they want: click a link, hand over data, or install malicious software.
They prey on human emotions and desires. Their tactics are calculated—and extremely effective. Targets range from government agencies and large enterprises to small businesses and everyday users.
❧ What’s the Goal of a Cyberattack? Popular Examples
Put simply, a cyberattack exploits security gaps to remotely access computer systems without authorization. The fallout can include:
-
Data or System Tampering/Destruction
Attackers infiltrate systems and introduce changes that cause chaos—manipulating financial data, altering system files, or even paralyzing a company’s IT infrastructure. A common example is ransomware, where hackers lock access to data and demand payment to restore it.
-
Theft and Exfiltration of Sensitive Documents
Many campaigns are designed to steal confidential information—financial records, business plans, and other strategic documents. Phishing—fake pages that trick users into entering their credentials—is one of the most common tools.
-
Disrupting Apps and Websites
DDoS (Distributed Denial of Service) attacks overwhelm servers with traffic, blocking normal access to websites or apps. For online businesses, the result can be significant financial loss and customer trust erosion.
-
Customer Data Breaches
One of the most dangerous consequences is the exposure of personal data—national IDs, addresses, credit card numbers, passwords. This harms a company’s reputation and puts users at risk of identity theft and fraudulent transactions.
-
Major Financial Losses
Attacks can cause direct and indirect losses: ransom payments, downtime, system rebuilds, churned customers. Banks, for instance, have lost millions to fraud and credential theft.
This list isn’t exhaustive. The damage can be catastrophic. Let’s be honest—when confidential government emails leak, losing a few hundred from your account seems minor by comparison.
❧ DDoS and Other Threats Used by Cybercriminals—The Most Common Attack Type
You’ve seen what attackers aim for; now let’s break down the typical techniques and malicious software they use.
❧ Malware (Malicious Software)
Attackers often send emails with payloads that infect machines and grant access to internal networks—sometimes degrading the entire environment. Common tools include trojans and spyware. One click is all it takes to invite an unwanted “guest” onto your device.
❧ Distributed Denial of Service (DDoS)
This floods a specific site or app with an enormous volume of requests. The overload blocks normal usage and can even crash servers.
A simpler variant, DoS, uses a single source rather than a distributed network.
❧ Phishing (Credential Theft & Impersonation)
Criminals impersonate real companies or public institutions to steal credentials and gain entry to corporate or personal networks—often via convincing emails or look-alike websites.
❧ SQL Injection
Luki w softwarze dają cyberprzestępcom duże pole manewru. Po wprowadzeniu modyfikacji doprowadzają nie tylko do wycieku danych, ale również oszustw finansowych.
❧ Botnets
Malware-infected devices—sometimes across the globe, sometimes within a private network—are chained together to perform attacker-controlled actions.
Symptoms include spam bursts and a barrage of pop-ups (think fake cookie notices or bogus alerts) that make devices barely usable.
❧ Cross-Site Scripting (XSS)
Attackers inject malicious code (e.g., JavaScript) into a web application that victims visit. Exploiting front-end flaws lets them harvest logins and personal data or redirect users to fake pages.
XSS can also seed infections on user devices, making it especially dangerous for high-traffic sites.
❧ Ransomware (Extortionware)
As the name suggests, this malware holds your data hostage. Criminals threaten to leak sensitive information or destroy valuable assets (e.g., company databases) unless you pay.
These are the most common types of cyber threats. Feeling a chill down your spine? Relax—you don’t have to be the next victim 👇
❧ Cybersecurity Basics—How to Detect Risks and Protect Against Attacks
No matter if you’re a CEO or an everyday user, you need a reliable security stack.
Choosing and installing trusted antivirus/endpoint protection is only the start. Regular updates are critical. Adversaries leverage sophisticated infrastructure; security vendors respond with continual improvements—use them.
Next, enable multifactor authentication (MFA). Retire birthdays and pet names as passwords. Use strong, unique passwords—ideally from a reputable password manager, across both computers and smartphones. These steps make it much harder to hijack, say, a social-media profile.
Finally, remember the perennial truth: people are the weakest link. You can’t maintain security without ongoing employee training—and a personal commitment to keep learning.
❧ A “Hacker Drill” for Your Company: Red Teaming
As we noted, improving cybersecurity is largely about raising human awareness.
This is especially true for employees on company hardware. In many organizations, the mindset “not my laptop, not my problem” still lingers.
Owners often grasp the scale only after a successful attack. To avoid learning the hard way, more and more companies use red teaming—a simulated hack to test staff awareness and organizational defenses. The result is a clear picture of how prepared you are for a real-world assault.
❧ Remember: Even the Biggest Threats Can Be Anticipated
Hackers aren’t Robin Hood 🏹 fighting “the system.”
Everyone online is a potential target—but risk can be reduced. Start with common sense and healthy skepticism. Don’t click strange links. Don’t open suspicious attachments. Keep software up to date, monitor regularly, and keep building your knowledge, preferably from reliable sources (like this piece you’re reading 😉).
At Kryptonum, we’re genuinely excited about cybersecurity—and when it comes to encrypting sensitive data, we charge in like a boar through raspberry bushes 🐗
You can be sure we’ll do everything we can to harden your website.

